eCX The Data Correspondence Architecture
eCX's trust architecture, in its data correspondence objective, mobilizes cybercrime machine event data of the highest reliability possible in a voluntary exchange scenario, an incentivizing schema framed two important ways
First, the eCX Data Sharing Agreement (DSA) establishes a best-efforts relationship between eCX users and the APWG to maximize the attention eCX users pay to data fidelity and categorization accuracy – without resorting to Service Level Requirements (SLA) that can make corporate counsel wary.
APWG's Data Sharing Agreement strikes an important balance to incentivize accurate & complete data contributions
At the same time, the eCX’s endogenous audit facility — allowing each member-contributed record with a marked confidence factor to be traced directly to an APWG member/submitter — makes every contributing eCX user accountable by design for every data element that they enter into the eCX clearinghouse.
Together, these provide the key instrumentation to incentivize eCX's enrolled users to to attend to data accuracy and categorization fidelity in all their submissions.
In these elemental but crucial ways, eCX’s data correspondence architecture programmatically promotes high reliability data contributions at a scale that can be expanded to any conceivable degree in order to meet and confront the expansion of cybercrime’s ever expanding reach.
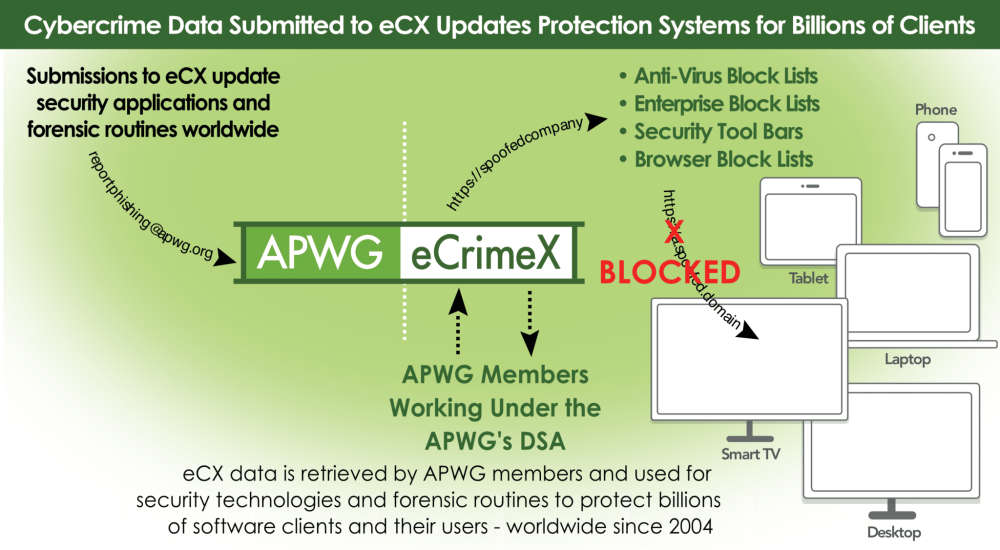
Every eCX user is accountable by design for every data element the member enters into eCX - key incentive for accuracy
The APWG’s eCX archives five data types on the API’s endpoints:
Phishing: The eCX receives hundreds to thousands of new, unique phishing URLs every day. The listings include confidence scores and brand (target) tags, so you can assess the data’s reliability. Learn about new attacks against hundreds of companies across the Internet, including the ones you need to protect.
Report Phishing: a repository of reported phishing emails, including header data, body text and images.
Malicious IPs: This feed contains IP addresses that have been recently observed as sources of malicious activity, such as fraudulent transactions and tell-tale port scanning.
Malicious Domains: An archive of maliciously registered domain names, including fake stores and fraud/identity theft websites. Supporting data can be added and forwarded to registrar and registry operators, or other APWG members, to aid in suspensions.
Cryptocurrency: This repository of problematic virtual currency addresses helps APWG members identify sources of malicious transactions and enrich your analytic tools. It’s high-value data for cryptocurrency exchanges, wallet providers, trading platforms, and investment funds who have to protect themselves and their customers against phishing and cybercrime. APWG members, to aid in takedowns.
Malicious SMS/Text: This repository of malicious text messages via SMS protocol and over-the-top text messaging service helps APWG members report and manage criminal texting.