APWG Q3 Report: Phishers Target Victims in New, Intrusive and Menacing Ways
Fraudsters Customizing Attacks with Victims’ Home Addresses and Images, Frightening Victims with Phone Calls and Text Messages
The APWG’s new Phishing Activity Trends Report reveals that scammers are approaching potential victims in very direct, often menacing ways, as growing numbers of fraudsters and extortionists personalize attacks to include photos of potential victims’ homes, while others use text messages and phone calls to make personal contact.

(c) 2024 APWG Studios
John Wilson, Senior Fellow, Threat Research at APWG contributing member Fortra, describes a new extortion technique that surfaced recently. “Previous extortion messages tended to be generic. We now see bad actors customizing their threats. Attack emails we began to see late in Q3 included the recipient’s phone number and home address as part of the lure. Many of these messages even contained a Google Street View image of the intended victim’s home.
Attack emails we began to see late in Q3 included the recipient’s phone number and home address as part of the lure. Many of these messages even contained a Google Street View image of the intended victim’s home. – John Wilson, Fortra
Online extortion is a scam in which the extortionist claims that he has embarrassing information about the victim – and demands money from him or her to prevent its distribution. While extortion scams have existed for years, the we-know-where-you-live angle is a disturbing new tactic, and makes the threat more vivid.
Matthew Harris, Senior Product Manager, Fraud at APWG contributing member OpSec, says that in Q3 the company detected a strong volume increase in two phishing techniques. One is vishing: voice phishing, where criminals use phone calls to steal personal information from victims. “Vishing incidents in Q3 increased more than 28 percent over Q2 volumes,” Harris says.
These phone-based methods are more immediate, and allow fraudsters to talk victims out of their sensitive information. The other was smishing incidents: phishing advertised via SMS and text messages. “Smishing increased more than 22 percent in the third quarter of 2024,” Harris says.
These phone-based methods are more immediate, and allow fraudsters to talk victims out of their sensitive information. – Matt Harris, OpSec
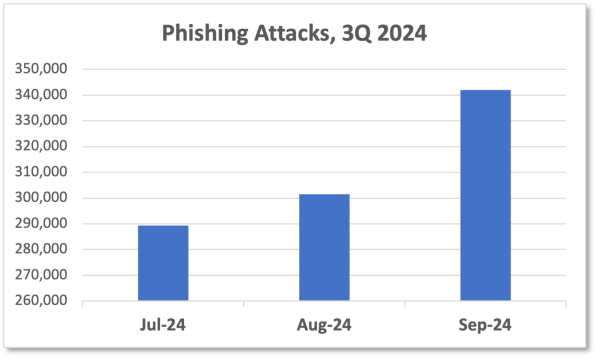
In the third quarter of 2024, APWG observed 932,923 phishing attacks, up from 877,536 in the second quarter. The number of phish reported to APWG has held steady since June 2023, varying between 290,000 and 370,000 attacks per month. APWG data curators note that email providers have been making it increasingly difficult for users to forward phishing to APWG and to other anti-abuse organizations and law enforcement authorities.

(c) 2024 APWG Studios
When fraudsters use email, they prefer to use free email services. Fortra found that 70 percent of Business Email Compromise (BEC) attacks in Q3 2024 were launched using a free webmail domain. (The remainder were deployed using a combination of maliciously registered domains and compromised email accounts.)

Google’s Gmail was by far the most popular free webmail provider for BEC scammers, used for 83.1 percent of the free webmail accounts that scammers set up for BEC scams in Q3 2024.
Fraudsters acquired the domain names that they used to run their BEC attacks at the following domain name registrars:

John Wilson of Fortra also noted: “Fortra observed a significant increase in the percentage of malware-laden messages reaching end-user inboxes in Q3 2024, with 12.3 percent of threat messages directing the recipient to a malicious payload. The most common malware family observed by Fortra was the Remcos RAT.”
The full text of the report is available here: https://docs.apwg.org/reports/apwg_trends_report_q3_2024.pdf
About the APWG
Founded in 2003, the Anti-Phishing Working Group (APWG) is the global industry, law enforcement, and government coalition focused on unifying the global response to electronic crime. Membership is open to qualified financial institutions, online retailers, ISPs and Telcos, the law enforcement community, solutions providers, multilateral treaty organizations, research centers, trade associations and government agencies. There are more than 2,200 companies, government agencies and NGOs participating in the APWG worldwide.
APWG’s apwg.org and stopthinkconnect.org websites offer the public, industry and government agencies practical information about phishing and electronically mediated fraud as well as pointers to pragmatic technical solutions that provide immediate protection. The APWG is co-founder and manager of the global STOP. THINK. CONNECT. campaign, most recently deployed as the national cybersecurity awareness campaign of Argentina, and founder/curator of the Symposium on Electronic Crime Research, the world’s only peer-reviewed, published conference dedicated specifically to electronic crime studies (https://ecrimeresearch.org/ecrime-symposium/). APWG advises hemispheric and global trade groups and multilateral treaty organizations such as the European Commission, the G8 High Technology Crime Subgroup, Council of Europe’s Convention on Cybercrime, United Nations Office of Drugs and Crime, Organization for Security and Cooperation in Europe, Europol EC3 and the Organization of American States. APWG is a member of the steering group of the Commonwealth Cybercrime Initiative at the Commonwealth of Nations.
Among APWG’s corporate sponsors are: AI Spera, Acronis, Adobe, AhnLab, AT&T, Arteria Communications, Allure Security, AREA 1, AIT, appgate, Apple, Asurion Insurance Services, Avast, Away AI, AXUR, BW CIRT, Bambenek Consulting, Banelco CSIRT, BanCERT, Bolster, Booz Allen Hamilton, BrandShield, Browlser, ByteDance, CHT Security, Canva, Central Bank of Jordan, Check Point, Cipherbit (Grupo Oesia), Cisco, CLARO, Cloudflare, Cloudmark, COFENSE, Coinbase, Comcast, CrowdStrike, CSC, CSIRT BANELCO, CSIS, Cyan Digital Security, Cyble, Cyren, Cyxtera, CZ.NIC, DS Lab, DigiCert, dmarcian, DocuSign, DNS Filter, DNS Belgium, EBRAND, Entrust Datacard, ESET, FirstRand, Fortinet, Fortra, FraudWatch, GetResponse, GMS Securidad, Group-IB, Guidewire, Hitachi Systems, .ID, ICANN, Identity Digital, Infoblox, Ingressum, INKY Technology Company, IQ Global, Kaspersky, KnowBe4, Lenos Software, LinkedIn, LINE, Looking Glass, LSEC, Material Security, McAfee, Meta, Mimecast, NCA, NAVER, Netcraft, NetSTAR, Nominet, Opera, OpSec Security, Palo Alto Networks, PANDI, PayPal, Proofpoint, Qintel, Rakuten, Recorded Future, Redsift, REDIRIS, ReversingLabs, RiskIQ, RSA, S2W Lab, SafeGuard Cyber, Salesforce, Secutec, Seven & i Holdings, Co. Ltd, SHRESHTA, SIDN, SlashNext, Sophos, Spamhaus Technology, SWITCH, Symantec, Telefonica, TEMU, Tessian, Thomsen Trampedach, ThreatSTOP, TNO, Tracer, TrendMicro, Trustwave, Twilio, Unbiased Security, Vade, Verisign, Viettel Cyber Security, WMC Global, Webroot, workday, ZeroFOX, ZibaSec, Zimperium, YARXIX, ZIX, .XYZ, and zvelo.
Contacts
For media inquiries related to the APWG, please contact APWG Secretary General Peter Cassidy (pcassidy@apwg.org, +1.617.669.1123). Or for company-specific content related to this release, please contact: Stefanie Wood Ellis of OpSec Security (sellis@opsecsecurityonline.com); Rachel Woodford of Fortra (Rachel.Woodford@fortra.com).